shodan.io
Ever wondered how you can find publicly accessible CCTV cameras? What about finding out how many Pi-Holes are publicly accessible? is your coffee machine publicly accessible? 🤣🤣🤣🤣🤣
Shodan.io is the answer!General Shodan Dorking
Shodan scans the whole internet and indexes the services run on each IP address.You must have a paid account on
shodan.io.
we can learn several things related to our search(if be Domain), such as:
- IP address
- hosting company
- geographic location
- server type and version
Some Fun Examples :
Which uses optical character recognition and remote desktop to find machines compromised by ransomware on the internet.
1
has_screenshot:true encrypted attention
1
encrypted
ICS and we can Discover Another Scada:
1
screenshot.label:ics
Internet connected machines vulenrable to heartbleed :
1
vuln:CVE-2014-0160
Solar Winds Supply Chain Attack by using Favicons:
1
http.favicon.hash:-1776962843
Shodan Extension
I imagine this is a good extension for any people interested in bug bounties, being quickly able to tell if a system looks vulnerable or not based on the Shodan output.
Explore Filters
EX :
1
asn:AS14061 product:MySQL
EX on Eternal Blue exploits :
1
vuln:MS17-010
Categories
EX :Pi-hole https://github.com/beesecurity/How-I-Hacked-Your-Pi-Hole/blob/master/README.md
Research
2000.shodan.io For Fun haha
Browse Search Directory
Shodan lets users share their search queries with the community by saving them to the search directory. Shodan doesn’t otherwise store or share your search queries. The queries in the search directory were explicitly shared by our users for the benefit of the community.
More Explore
Explore all SubDomain & Directory in Shodan
Very useful
https://www.shodan.io/explore/recent
Favicon Map
you can explore header http hahaha
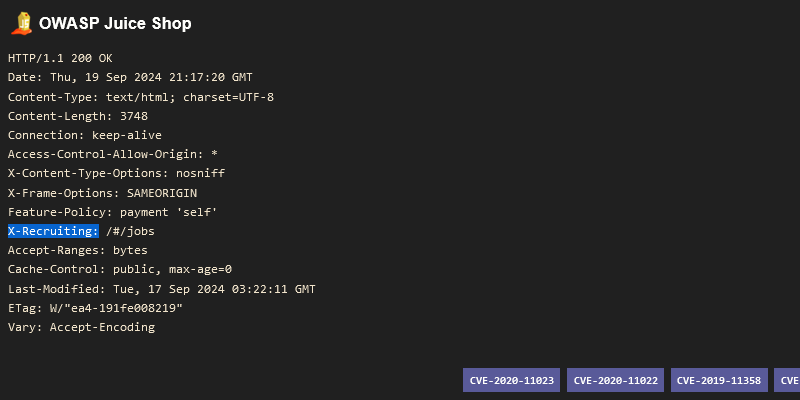
https://www.shodan.io/search?query=%22X-Recruiting%3A%22
and more more
https://www.shodan.io/search?query=ethereum+hashrate
https://www.shodan.io/search?query=airplay+port%3A5353
https://www.shodan.io/search?query=%22HID+VertX%22+port%3A4070
1
https://www.shodan.io/explore/popular?page=`Such-IDOR`
risk assessment
Finding services
Let’s say we are performing a pentest on a company, and we want to find out what services one of their servers run.
We need to grab their IP address. We can do this using ping.
1
ping tryhackme.com
We can ping tryhackme.com and the ping response will tell us their IP address.
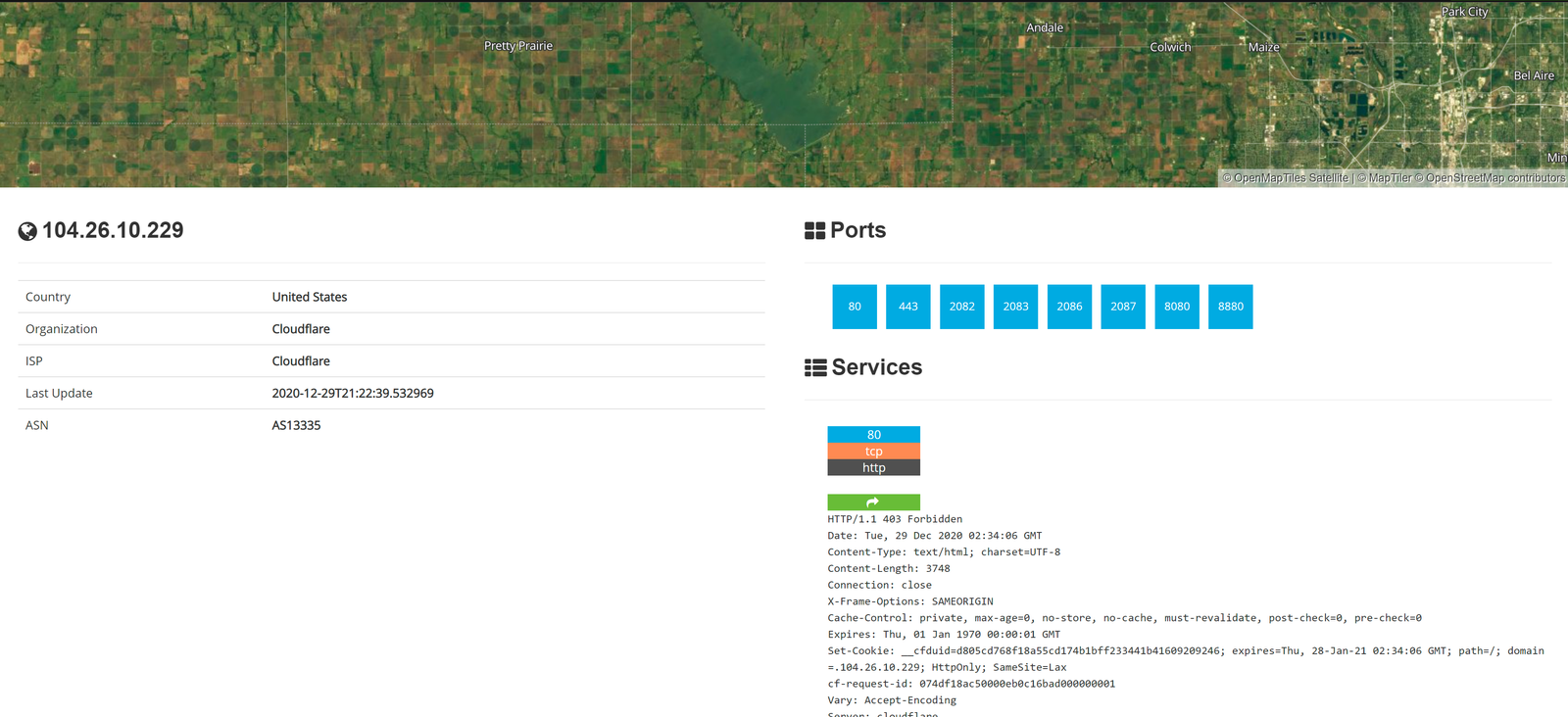
Then once we do this, we put the IP address into Shodan to getWe can see that TryHackMe runs on Cloudflare in the United States and they have many ports open.
Cloudflare acts as a proxy between TryHackMe and their real servers.if we were pentesting a large company, this isn’t helpful. We need some way to get their IP addresses.
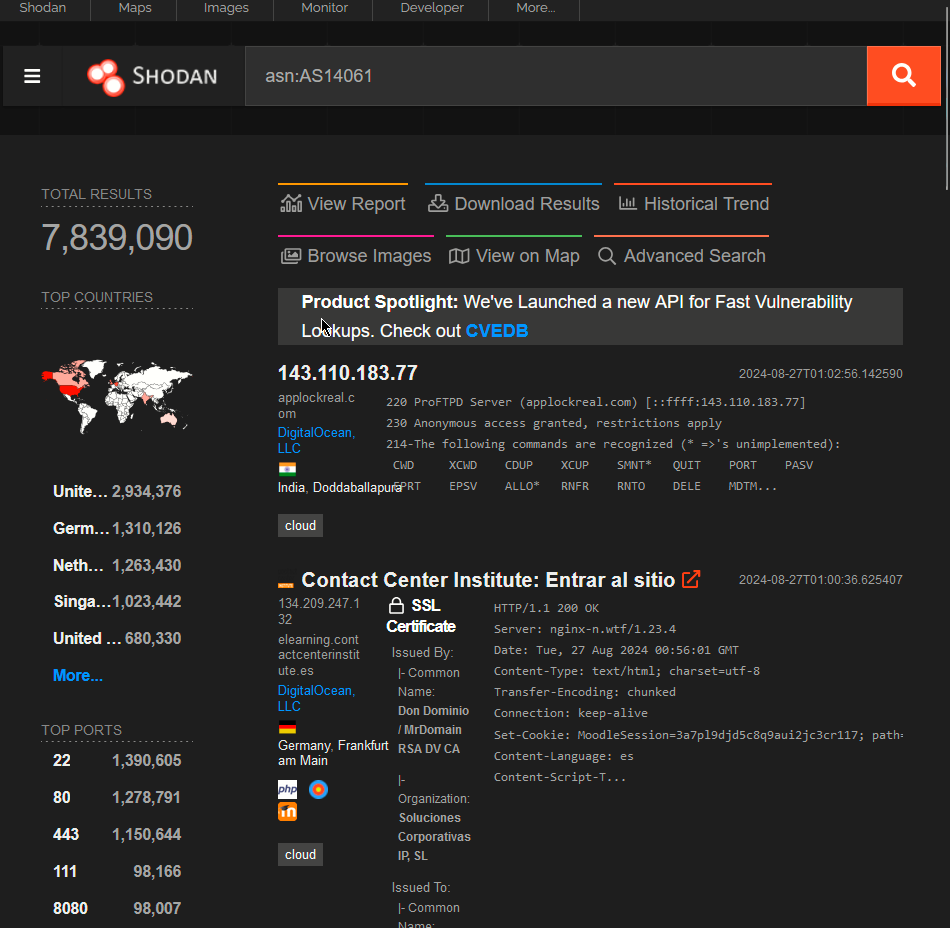
We can do this using Autonomous System Numbers(ASN)
If you are an enormous company like Google you will likely have your own ASN for all of the IP addresses you own.
Which tells us they have the ASN AS14061 in this case.
Tryhackme isn’t a mega large corporation, so they don’t own their own ASN. When we google AS14061 we can see it is a DigitalOcean Organizations ASN number.
On Shodan.io,we can search using the ASN filter :
1
ASN:[NUMBER]
in this case:
1
ASN:AS14061
OR with engine search such google :
1
https://www.shodan.io/search?query=asn%3AAS14061
Doing this, we can see a whole range 7.8 million websites, in fact) that are on this one single ASN!
Knowing the ASN is helpful, because we can search Shodan for things such as coffee makers or vulnerable computers or webcam and more within our ASN, which we know (if we are a large company) is on our network.
hostname
1
hostname:ju.edu.jo
Find in hosts
1
https://www.shodan.io/host/87.236.235.122
We can put the IP address into an ASN lookup tool such as below
https://hackertarget.com/as-ip-lookup/
https://mxtoolbox.com/asn.aspx
https://mxtoolbox.com/SuperTool.aspx => for multi things OR with shodan direct
https://mxtoolbox.com/NetworkTools.aspx
Banners
Devices run services, and Shodan stores information about them. The information is stored in a banner. It’s the most fundamental part of Shodan.
1
2
3
4
5
6
7
8
9
10
11
import shodan
# Initialize the API
api = shodan.Shodan('YOUR_API_KEY')
# Search for a specific banner
results = api.search('"Welcome to nginx!"')
# Print the results
for result in results['matches']:
print(f"IP: {result['ip_str']}, Banner: {result['data']}")
Another example, using the Shodan Python API, you can retrieve banner information for a specific IP like this :
1
2
3
4
5
6
7
8
9
10
# Make sure your script is named something like 'my_shodan_script.py'
import shodan
api = shodan.Shodan('YOUR_API_KEY')
# Lookup the banner for a specific IP
host = api.host('46.252.132.235')
print(host['data'])
renaming the script and cleaning up the cache, run your script again to see if the issue is resolved.
1
rm -rf __pycache__
Advanced Queries: You can also use more advanced queries to filter results by port, country, or device type. For example:
1
port:80 "Server: Microsoft-IIS"
all the metadata that Shodan crawlers gather. It is the reference document for all information about top-level properties that are available on the banner.
These top-level properties contain service-specific information that provide deeper insights into the configuration and deployment of a device
https://datapedia.shodan.io/#search
https://datapedia.shodan.io/#sample
https://datapedia.shodan.io/banner.schema.json
https://www.shodan.io/search/advanced
EX of Property and exited more more:
https://datapedia.shodan.io/property/_shodan.html
https://datapedia.shodan.io/property/cobalt_strike_beacon.html
products
https://www.shodan.io/about/products
There are 2 APIs for accessing Shodan:
- The REST API: provides methods to search Shodan, look up hosts, get summary information on queries and a variety of utility methods to make developing easier.
- The Streaming API: provides a raw, real-time feed of the data that Shodan is currently collecting. There are several feeds that can be subscribed to, but the data can’t be searched or otherwise interacted with; it’s a live feed of data meant for large-scale consumption of Shodan’s information.
Shodan API
The InternetDB API
Fast IP Lookups for Open Ports and VulnerabilitiesEX :
https://internetdb.shodan.io/8.8.8.8
Real Scenariohttps://internetdb.shodan.io/85.159.218.187
Another API
https://developer.shodan.io/api
https://developer.shodan.io/api/stream
https://developer.shodan.io/api/requirements
https://developer.shodan.io/api/clients
https://developer.shodan.io/api/trends
Filters Cheat Sheet
Shodan currently crawls nearly 1,500 ports across the Internet. Here are a few of the most commonly-used search filters to get started.
We Can Combine 2,3 etc... of Filters| Filter Name | Description | Example |
|---|---|---|
| city | Name of the city | Devices in San Diego |
| country | 2-letter Country code | Open ports in the United States |
| http.title | Title of the website | “Hacked” Websites |
| net | Network range or IP in CIDR notation | Services in the range of 8.8.0.0 to 8.8.255.255 |
| org | Name of the organization that owns the IP space | Devices at Google |
| port | Port number for the service that is running | SSH servers |
| product | Name of the software that is powering the service | Samsung Smart TVs |
| screenshot.label | Label that describes the content of the image | Screenshots of Industrial Control Systems |
| state | U.S. State | Devices in Texas |
| hostname | lookup a real IP websites , CVE of Organizations | websites |
ISO 3166-1 alpha-2 codes are two-letter country codes.
General
- all
- asn
- city
- country
- cpe
- device
- geo
- has_ipv6
- has_screenshot
- has_ssl
- has_vuln
- hash
- hostname
- ip
- isp
- link
- net
- org
- os
- port
- postal
- product
- region
- scan
- shodan.module
- state
- version
Screenshots
- screenshot.hash
- screenshot.label
Cloud
- cloud.provider
- cloud.region
- cloud.service
HTTP
- http.component
- http.component_category
- http.favicon.hash
- http.headers_hash
- http.html
- http.html_hash
- http.robots_hash
- http.securitytxt
- http.status
- http.title
- http.waf
Bitcoin
- bitcoin.ip
- bitcoin.ip_count
- bitcoin.port
- bitcoin.version
Restricted
The following filters are only available to users of higher API plans.
- tag
- vuln
SNMP
- snmp.contact
- snmp.location
- snmp.name
SSL
- ssl
- ssl.alpn
- ssl.cert.alg
- ssl.cert.expired
- ssl.cert.extension
- ssl.cert.fingerprint
- ssl.cert.issuer.cn
- ssl.cert.pubkey.bits
- ssl.cert.pubkey.type
- ssl.cert.serial
- ssl.cert.subject.cn
- ssl.chain_count
- ssl.cipher.bits
- ssl.cipher.name
- ssl.cipher.version
- ssl.ja3s
- ssl.jarm
- ssl.version
NTP
- ntp.ip
- ntp.ip_count
- ntp.more
- ntp.port
Telnet
- telnet.do
- telnet.dont
- telnet.option
- telnet.will
- telnet.wont
SSH
- ssh.hassh
- ssh.type
EXAMPLES
Click on Search to go directly to the Browser.
Basics
SearchWebsites that require HTTPS connections
1
HTTP Strict-Transport-Security
SearchApache web servers
1
product:Apache
SearchServices that have the word “Apache” in their headings
1
Apache
SearchServices with a hostname containing either “google.com” OR “facebook.com”
1
hostname:google.com,facebook.com
HTTP filters
SearchWebsites that have the word “Apache” in their HTML
1
http.html:Apache
SearchWebsites that are using the Bootstrap CSS framework
1
http.component:bootstrap
SSL filters
SearchWebsites that support TLS 1.3
1
ssl.version:tlsv1.3 HTTP
SearchServices that support SSLv2 and don’t support TLS
1
ssl.version:sslv2 -ssl.version:tlsv1,tlsv1.2,tlsv1.3
SearchNon-HTTPS SSL services that were issued a certificate for *.google.com
1
ssl.cert.subject.cn:google.com -HTTP
SearchWebsites that support HTTP/2
1
ssl.alpn:h2
SearchSSL services (HTTPS, SMTPS, POP3S etc.) that were issued a certificate for *.google.com
1
ssl.cert.subject.cn:google.com
SSH filters
SearchSSH on port 22 OR 3333
1
ssh port:22,3333
SearchSSH on non-standard ports
1
ssh -port:22
Screenshot filters
SearchPublic VNC services hiding behind common web ports
1
has_screenshot:true rfb disabled port:80,443
SearchIndustrial control systems identified using machine learning
1
screenshot.label:ics
SearchSearch the OCR in Remote desktops for compromised by ransomware
1
has_screenshot:true encrypted attention
Restricted filters
SearchIndustrial control systems running an industrial protocol (i.e. no web servers)
1
tag:ics
SearchServices that are vulnerable to Heartbleed
1
vuln:CVE-2014-0160
SearchCitrix devices in Germany, Switzerland or France that are vulnerable to CVE-2019-19781
1
vuln:CVE-2019-19781 country:DE,CH,FR
Shodan Monitor
The interesting part is that you can actually monitor other peoples networks using this. For bug bounties you can save a list of IPs and Shodan will email you if it finds any problems.
Note: This is a premium product, but you can often get $1 Shodan accounts on their Black Friday deals.
Shodan Monitor is an application for monitoring your devices in your own network. In their words:
Keep track of the devices that you have exposed to the Internet. Setup notifications, launch scans and gain complete visibility into what you have connected.
Previously we had to do this using their API, but now we have this fancy application.
Access the dashboard via this link:
https://monitor.shodan.io/dashboard
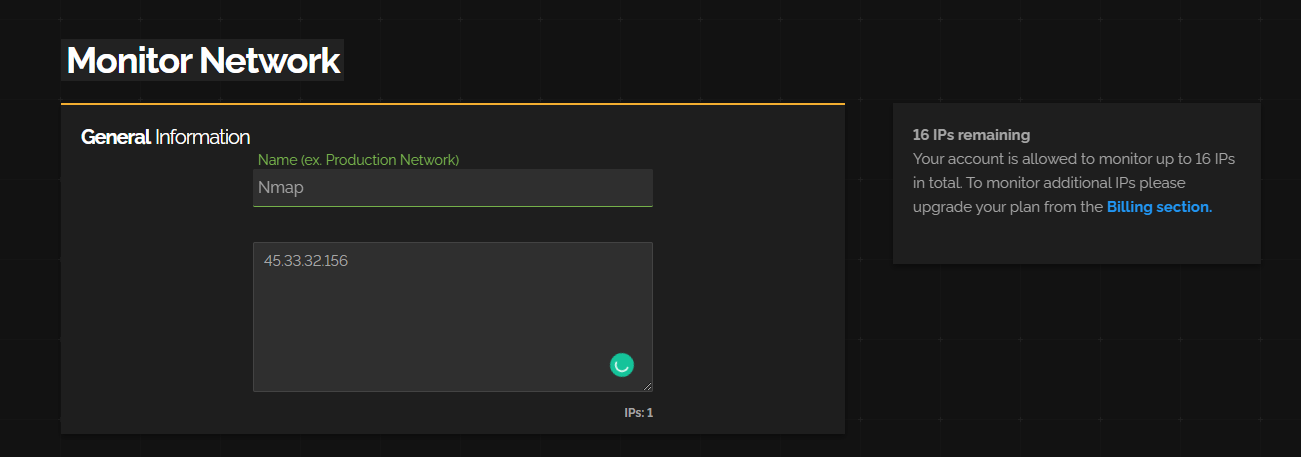
You’ll see it’s asking for an IP range.
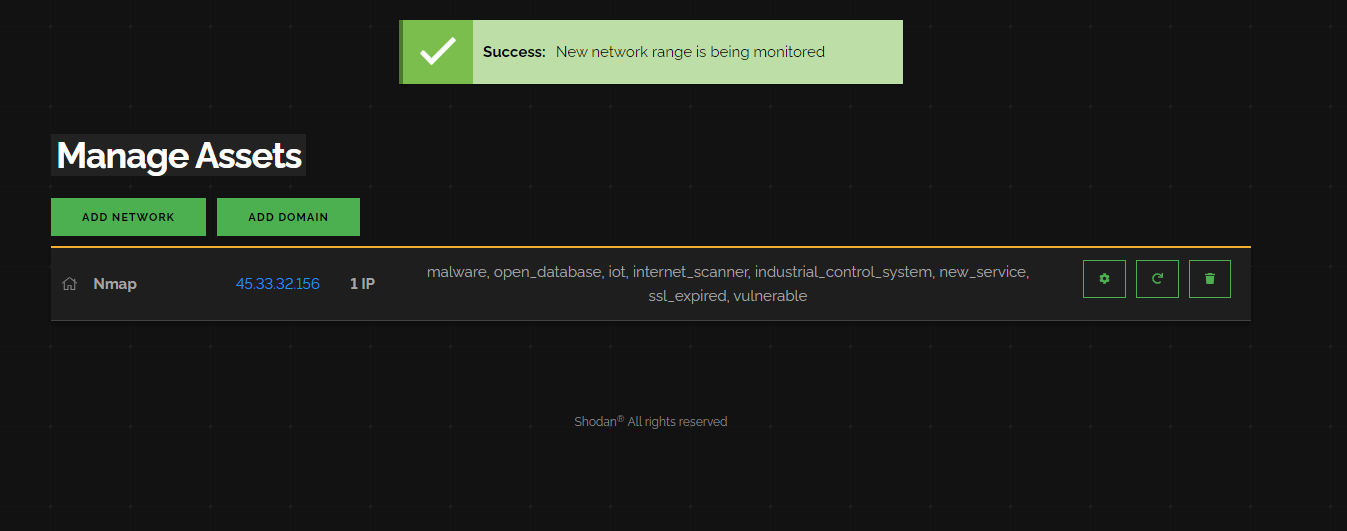
Once we add a network, we can see it in our dashboard.
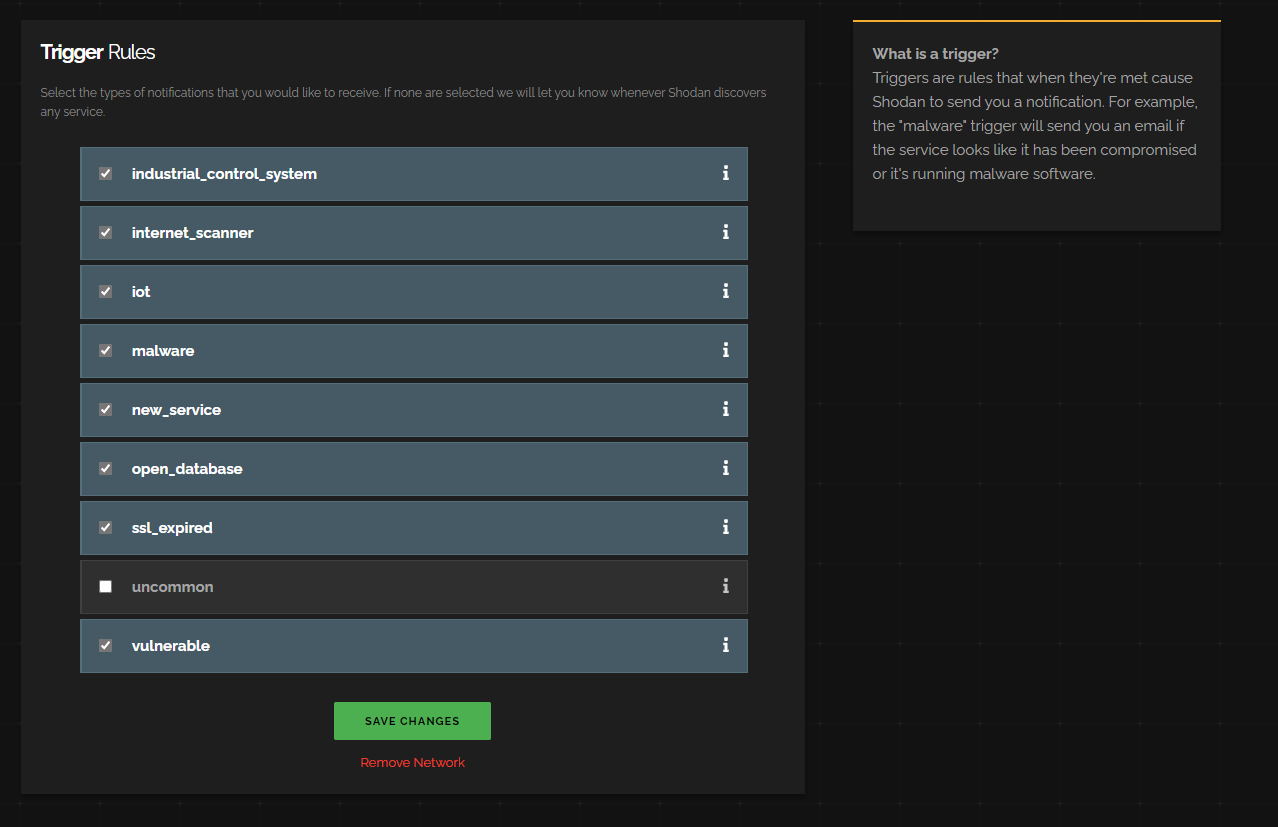
If we click on the settings cog, we can see that we have a range of “scans” Shodan performs against our network.
Anytime Shodan detects a security vulnerability in one of these categories, it will email us.
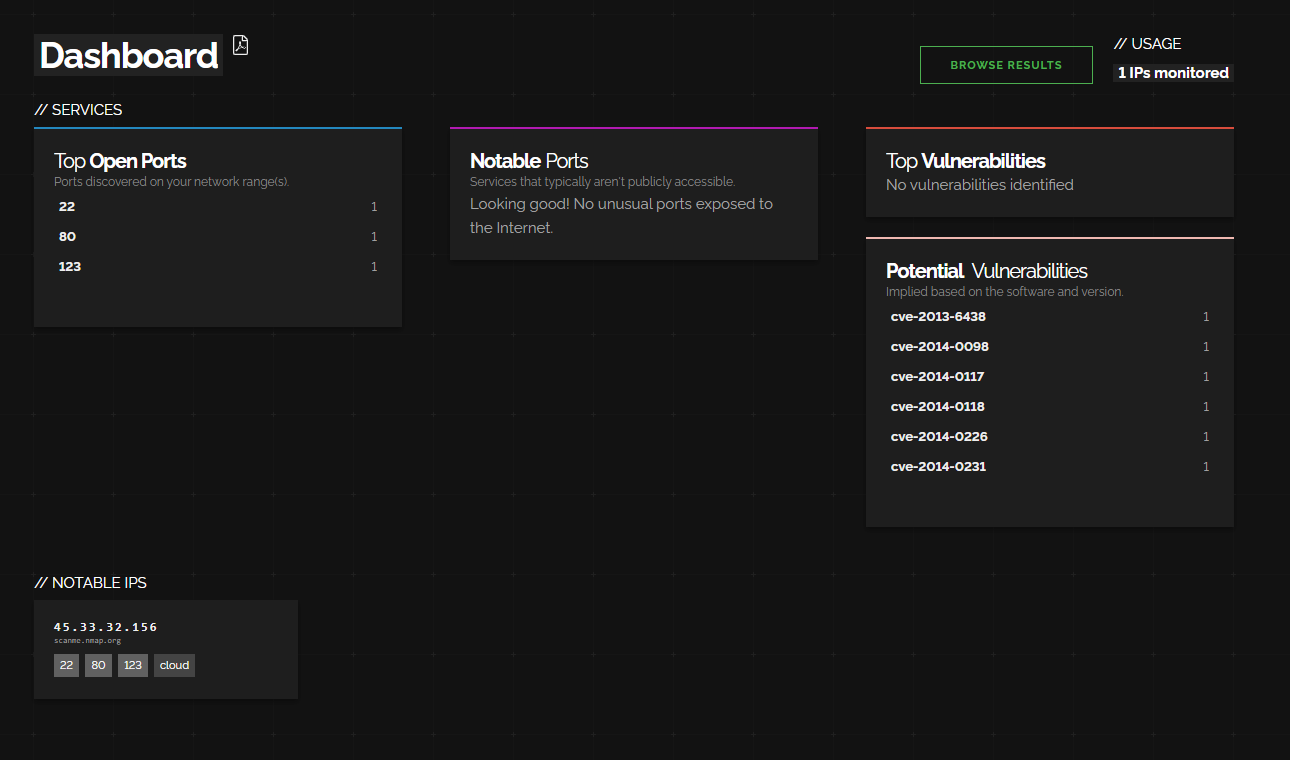
If we go to the dashboard again we can see it lays some things out for us.
Most notably:
- Top Open Ports (most common)
- Top Vulnerabilities (stuff we need to deal with right away)
- Notable Ports (unusual ports that are open)
- Potential Vulnerabilities
- Notable IPs (things we should investigate in more depth).
Mastering Shodan Search Engine
Let’s explore the depths of Shodan Dorking to level up your security testing. While Google can find many websites, Shodan lets you find everything else – servers, webcams, washing machines, etc. Imagine that you are a bad guy. It could be a true gold mine! But of course, I do not endorse anything illegal! The main thing that I’m trying to teach – is the methods to get some good leads, to find something that it’s critical for certain organizations. Report those findings and might get some reward or recognition AKA Bounties.
Watch this video in case you are too lazy to read 😊
Preparation
I’ve been doing recon on the Coca-Cola Company. Even before deep diving into the Shodan, I highly suggest gathering some information about the company. One of the prerequisites is getting the company name. You could either get it via services like crt.sh, visiting the main website and inspecting the certificate, or just checking the footer of the main page. For this particular session, I will use “the Coca-Cola Company” as the organization name.
Basic keywords
The first keyword I like to use while doing Shodan Dorking is org with the company name. It is very helpful when testing for large companies or organizations. For this instance, the Coca-Cola Shodan dork will look like this:
1
org:"Coca-Cola Company"
Note: Even if you find some results, it doesn’t mean that it will actually belong to the company. Every time before you do something to the target, you have to validate.
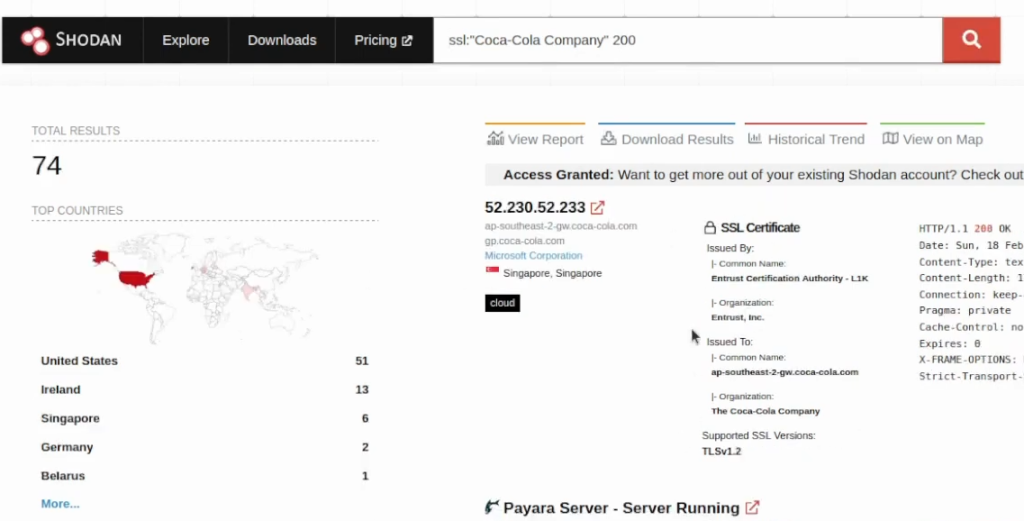
In this case, there are only 71 results to work on, so I suggest trying the next Shodan Dork – ssl:
1
ssl:"Coca-Cola Company"
If you want to exclude results with 403 or 400, you could use 200 to get like less results:
1
ssl:"Coca-Cola Company" 200
Alternatively, for SSL check you could try using ssl.cert.subject.CN:"target.com" dork, where target.com is your target’s root domain. For this specific case, the Shodan query for the main subdomain will look like this:
1
ssl.cert.subject.CN:"coca-cola.com"
Filtering Results
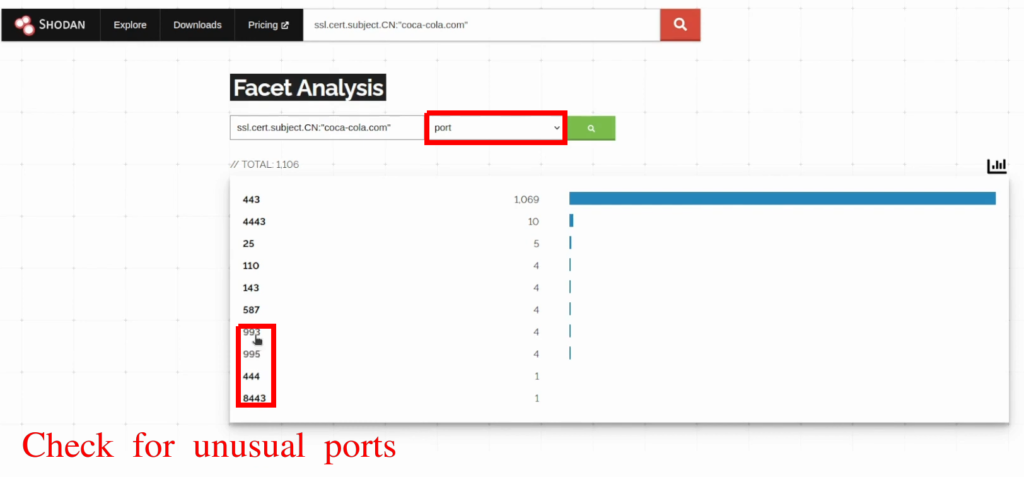
If you are getting thousands of results, your next goal is just to filter them out to only leave those that are interesting. I usually click on More… near TOP COUNTRIES or TOP PORTS:
You will be redirected to the page, where you can basically filter out the results. For example, by the port:
Another interesting filter is http.title:
Favicon Searches
Another interesting thing that you can also do – is search by favicon. If you have noticed Coca-Cola has its own favicon. When you have a lot of results, you can click on the icon itself and it will appear at the end of the query with http.favicon.hash<hash:
Later you could remove other filters, and check if you can enumerate more results just by using this hash. Another way to find this favicon hash is just from the main website by using extensions like fav-up.
Resources For Shodan Dorking
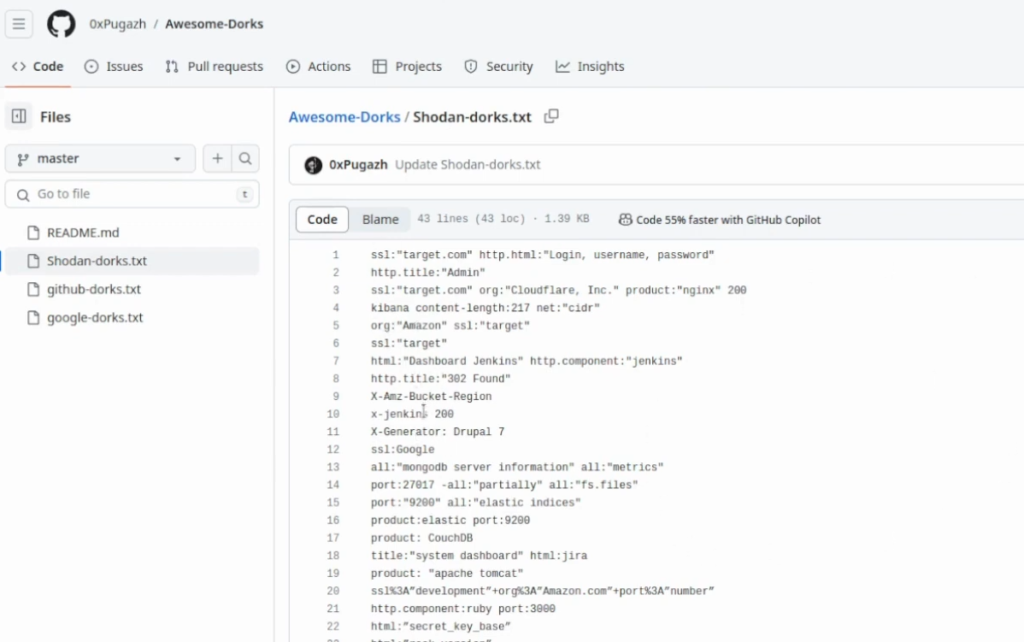
Search on github or google about shodan dorkinghttps://github.com/0xPugal/Awesome-Dorks/tree/master
https://github.com/jakejarvis/awesome-shodan-queries
When it comes to getting ideas, I have multiple favorite places to look for. The first one is the Awesome-Dorks repository on GitHub:
https://book.martiandefense.llc/notes/security-research/shodan-dork-cheatsheet
https://cheatography.com/sir-slammington/cheat-sheets/shodan/
https://denizhalil.com/2023/12/19/shodan-search-queries-cheat-sheet/
https://github.com/coreb1t/awesome-pentest-cheat-sheets/blob/master/docs/shodan.md
https://thor-sec.com/cheatsheet/shodan/shodan_cheat_sheet/
It’s pretty useful for Bug Bounty. There are some extra searches like – by the header. For example, checking for Jenkins – html:”Dashboard Jenkins” http.component:”jenkins”. This keyword checks in the HTML. Not all of Shodan dork repos on GitHub are useful since not all of those are made for bug bounties, but this repository is extremely helpful.
The next thing that I also use is checking for Shodan favicon hashes:
Certain products, like Jenkins, has their like the same hash everywhere. Atlassian has its own hash and sometimes even multiple different ones.
Lastly, my favorite way to get ideas for Shodan Dorking is from Twitter. I use Google for this – site:twitter shodan dorks:
SCADA Systems with Shodan
SCADA Hacking: Find Vulnerable SCADA Systems with Shodan
1
https://www.shodan.io/search?query=ics
1
https://images.shodan.io/?query=screenshot.label%3Aics
As you know, Shodan just scans the IP addresses around the world and then shows us the banners. We can then query through Shodan the parameters revealed in these banners to find IP addresses of a specific type of device.
In this guide, we will look for SCADA devices. SCADA or Supervisory Control and Data Acquisition are systems used for things like power transmission systems, nuclear plants, chemical plants, water treatment plants, HVAC systems, home heating, etc. All of these systems have digital controls, all of which are vulnerable to attack.
SCADA systems are a huge concern for national defense agencies, as a nation that has had its SCADA systems hacked will be left behind in the event of war. This is why organizations like US Homeland Security are so concerned about SCADA security. Most cyber warfare experts expect that all future wars will have a SCADA cyber attack component.
Table of Contents